Android Phone: Each family in this current world with a web association has known about this gadget called the Router. A switch essentially goes about as a guard to our web.
It is additionally equipped for getting our association. Thus it is imperative to defend it with a secret word to abstain from any hacking.
There are examples where switches have been hacked to get to individual data. There have been episodes experienced in the United States where switches have been hacked unlawfully to extricate information out of ordinary citizens.
While changing passwords and securing your Router is important, there are different alternatives that one should consider. Henceforth assuming responsibility for your framework gets critical now.
Numerous moral programmers have investigated alternatives to take control and offer simple approaches to abuse switches.
You may not know, yet the actual Router a scaled-down PC (if you may call it). It has its framework set up that works in an orderly and legitimate manner.
As PCs can be hacked, switches are likewise at an extraordinary danger of meeting a similar destiny.
IP Router:
The market is causing some upheaval around RouterSploit. It permits one to abuse a Router utilizing an unrooted Android phone, as per IPRouterlogin.
Moral programmers have thought of a different method that encourages one to protect their web bubble. Nonetheless, these procedures may have all the earmarks of being convoluted toward the starting once the essential establishment is finished.
At that point, the remainder of the capacities is a cakewalk.
Establishing your gadget can be a dangerous alternative. There is a termination of assurance and guarantee on established telephones.
Along these lines, choices to abuse switches on an unrooted gadget is something that needs a smidgen of work-around.
One such arrangement is – GNURootDebian. This application will assist you with accomplishing what you couldn’t prior with an established telephone.
What You Need to Get Started
The excellence of this arrangement is that you need an Android phone. I’m utilizing a Samsung Galaxy S8 because hauling around a monster curve screen glass helps me remember how delicate life is.
However, you can use any Android phone that upholds GNURoot Debian.
Download “GNURootDebian”
To make Debian Linux run on an unrooted gadget, download “GNURootDebian” from Google Play Store.
There will be some auto-run things that will look through the screen. When the looking over stops, we are prepared to continue.
Introduce a few conditions
There is a need to introduce a few conditions to make this whole construction work. It is proposed that you use python for the ideal module. Here are a few orders that you would require.
- well-suited get an update
- well-suited get introduce sudo
- sudo well-suited get introduce git-center
- Sudo well-suited get introduce python-dev-python-pip libncurses5-dev git
Download/introduce RouterSpoilt
The subsequent stage is to download/introduce RouterSpoilt. The following is a connection to the Github archive that will assist you with the set-up
https://github.com/invert shell/routersploit
Run nonexclusive Commands
Since you have downloaded it. The RouterSploit is prepared for its initial run. There are some more nonexclusive orders that you need to run:
- disc routersploit
- sudo python./rsf.py
Orders will show up.
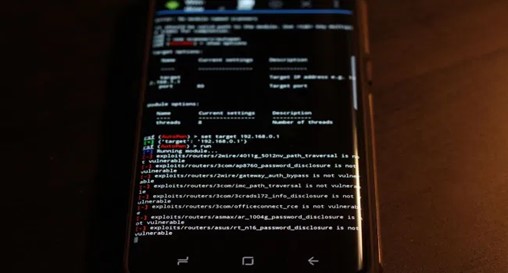
There are a few “arrange” that will currently show up on the screen. It is simple for the client to utilize the interface. ‘use,’ ‘set,’ ‘show alternatives,’ ‘check,’ ‘run.’
Select a Secret stage
The genuine work presently starts. Suppose you wish to set and arraign an objective. Here are a few things that you need to do.
This may appear to be somewhat scary regardless, yet clients get the hang of it after some time. At the point when you will get to something many refer to as the “WIFI cluster,”.
There will be a necessity of choosing a mysterious stage, about which you can learn better on the off chance that you read this top to the bottom article. Whenever you have recognized your IP address, utilize the accompanying orders to continue further.
- show choices
Need an exchanging IP address
Presently, we need to set an IP address to which it needs to switch.
- set objective IP_address_here
This IP changing is essential that would assist you with securing your present location consistently. When the exchanging is finished, run the module. At that point, it will move through every one of the available shortcomings.
Time to exploit
Whenever you have caught every one of the essential shortcomings, the time has come to abuse them. Some more orders can assist you with this movement.
- use abuses/cameras/dlink/dcs_9301_9321_auth_bypass
Check whether fruitful
It is the ideal opportunity for you to look at if your cycle has gone to be fruitful. There is a catch called “check,” which would permit you to a twofold check. You can rehash these means to misuse the given switches now and again.
Conclusion
This is one of the numerous techniques in which you can utilize an unrooted android phone, which would permit you to assault any switch you wish to control.
While RouterSploit is outstanding amongst other accessible alternatives for an unrooted gadget. There are different alternatives accessible in an alternate climate, specifically, Metasploit. RouterSploit, notwithstanding, has demonstrated to be effective and straightforward to utilize.
Simultaneously, this empowers a lot of moral programmers to protect their switches through a cell phone. We need to comprehend that abuse can get one into a lot of legitimate issues.